Cybersecurity for Everyone: Software and Devices to Stay Safe. Navigating the digital world safely is more important than ever. From protecting your personal data to avoiding scams, this guide will equip you with the knowledge and tools to stay secure online. We’ll cover everything from choosing the right software to building a strong online presence.
This comprehensive guide will cover the essentials of cybersecurity, helping you understand the various threats and how to mitigate them. We’ll explore practical steps to secure your devices, manage passwords effectively, and protect your data. Learning about cybersecurity is not just about knowing the risks, but also about understanding the best practices to implement them in your everyday life.
Introduction to Cybersecurity
Staying safe online is like navigating a bustling city. You need to be aware of your surroundings and potential dangers to avoid getting lost or robbed. Cybersecurity is the digital equivalent of that awareness. It’s the practice of protecting your digital life from threats, from sneaky hackers to harmful viruses. In today’s hyper-connected world, cybersecurity isn’t just a good idea; it’s a necessity.
The digital world has opened up incredible opportunities, but it also comes with risks. Protecting your personal information, financial data, and devices is paramount. Knowing the common threats and how to defend against them empowers you to stay safe in the digital landscape. This is your guide to understanding cybersecurity and taking proactive steps to protect yourself.
Defining Cybersecurity
Cybersecurity is the collective effort to protect digital systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It encompasses a wide range of measures, from strong passwords to advanced encryption protocols.
Importance of Cybersecurity in the Digital Age
Cybersecurity is crucial in today’s digital world because our lives are increasingly intertwined with technology. From banking to shopping to social interactions, we rely on digital systems for almost everything. Compromising these systems can lead to significant financial losses, identity theft, and emotional distress.
Common Cybersecurity Threats
Individuals face a multitude of cybersecurity threats. These threats can range from seemingly harmless pranks to sophisticated attacks designed to steal valuable information. Recognizing these threats is the first step towards protection.
Types of Cybersecurity Threats
| Threat Type | Description | Example |
|---|---|---|
| Malware | Malicious software designed to harm or disrupt a system. This includes viruses, worms, Trojans, ransomware, and spyware. | A virus that infects your computer and steals your personal information. |
| Phishing | A social engineering technique where attackers impersonate legitimate entities (like banks or social media platforms) to trick victims into revealing sensitive information. | An email that appears to be from your bank asking for your login credentials. |
| Social Engineering | Manipulating individuals into divulging confidential information through psychological tactics. This often involves exploiting trust, fear, or curiosity. | A hacker posing as a technical support representative to gain access to your computer. |
| Denial-of-Service (DoS) Attacks | Overwhelming a system with traffic to prevent legitimate users from accessing it. | A website being bombarded with traffic, making it unavailable to users. |
| Man-in-the-Middle (MitM) Attacks | Intercepting communications between two parties without their knowledge, allowing attackers to eavesdrop or manipulate the exchange. | A hacker intercepting your online banking transaction and redirecting it to their own server. |
Software for Enhanced Security: Cybersecurity For Everyone: Software And Devices To Stay Safe

Source: twimg.com
Protecting your digital life is crucial, whether it’s strong passwords or updated software. But safeguarding the planet is just as important! Think about your beach trips and the impact you have on the environment. Checking out eco-friendly options for swimwear and gear, like reusable bags and biodegradable sunscreen, is a great way to start. Sustainable Swim: Eco-Friendly Options for the Beach offers some seriously cool ideas.
Ultimately, both protecting our digital and physical worlds requires mindful choices, from the software we use to the products we consume. This translates to responsible actions that benefit everyone.
Staying safe online is like having a superhero cape for your digital life. But unlike a cape, you need more than just willpower – you need the right tools. Luckily, a ton of reliable software applications are out there to bolster your defenses and keep your data secure. These tools are your digital shield, safeguarding your devices from the ever-present threat of malware and cyberattacks.
The digital world is a battlefield, and you need the right weapons. Software is your shield, your sword, and your impenetrable fortress against cyber threats. Investing in robust security software is a crucial step towards a safer, more secure online experience. It’s like installing a super-powered antivirus to keep your digital kingdom safe from intruders.
Popular and Reliable Security Applications
Various applications are available to bolster your digital security. These applications range from simple antivirus programs to comprehensive suites that offer protection against a wide array of threats. Understanding the features and benefits of these applications is key to choosing the right one for your needs. It’s like selecting the perfect superhero costume – you need one that fits your style and offers the best protection.
Features and Benefits of Antivirus Software
Antivirus software acts as a vigilant guard, constantly scanning your system for malicious programs like viruses, worms, and Trojans. It’s like having a digital security guard on patrol 24/7. These programs use a variety of techniques, including signature-based detection and heuristic analysis, to identify and neutralize threats. Features like real-time protection, scheduled scans, and automatic updates are essential for continuous defense. Real-time protection is like having a security system that alerts you immediately when something suspicious happens.
Comparison of Different Antivirus Solutions
Different antivirus solutions cater to various needs and budgets. Some offer comprehensive protection, while others focus on specific threats. Choosing the right solution depends on factors like the complexity of your digital environment and your financial capacity. Comparing features, performance, and user reviews can help you select the best antivirus solution for your device. It’s like choosing the right car for your needs – a sedan might be perfect for commuting, but a truck might be better for hauling heavy items.
Software Options for Protecting Against Malware
| Software | Pros | Cons |
|---|---|---|
| Kaspersky | Strong malware detection, reliable protection, available in various packages. | Can sometimes be resource-intensive, interface might not be as intuitive as some competitors. |
| Norton | Known for its user-friendly interface, comprehensive protection, broad range of features. | Potential for high resource consumption, some features might be unnecessary for average users. |
| Bitdefender | Fast scanning speed, high detection rates, effective at blocking phishing attempts. | Some users find the interface slightly less intuitive than others. |
| McAfee | Widely recognized name in the security industry, known for real-time protection. | Pricing structure might be less transparent than competitors, resource consumption can vary. |
Choosing the right software involves carefully evaluating its pros and cons in relation to your needs. The table above offers a concise overview of popular choices, allowing you to weigh your options and make an informed decision. It’s like comparing different restaurant menus to find the one that best suits your dietary preferences.
Password Management Software and Cybersecurity
Password management software plays a crucial role in modern cybersecurity. It simplifies the process of creating and storing strong passwords, mitigating the risk of compromised accounts. Using strong and unique passwords for each account is vital for preventing unauthorized access. Password managers generate complex, unique passwords for every site, which makes it much harder for hackers to crack your accounts.
Recommended Security Software by Device Type
- Computers: Norton AntiVirus, Kaspersky Internet Security, Bitdefender Antivirus Plus. These offer comprehensive protection against a wide range of threats for desktops and laptops.
- Mobile Devices: Trend Micro Mobile Security, Lookout, McAfee Mobile Security. These solutions provide robust protection against malware and other threats on smartphones and tablets.
- Internet of Things (IoT) Devices: Sophos Home Premium, F-Secure Home. These solutions address the specific security needs of interconnected devices. It’s important to protect even smart home devices.
These recommendations cater to diverse needs, offering a range of solutions for different types of devices. It’s like having a tailor-made suit for every member of your family.
Device Security Best Practices
Protecting your digital life is like safeguarding your physical one – crucial for peace of mind. Your devices, be it a laptop, phone, or tablet, are gateways to your personal information, banking details, and precious memories. Robust security practices are paramount to keeping this information safe from prying eyes and malicious actors.
Importance of Device Security
Device security is not just about preventing theft; it’s about protecting your sensitive data from cybercriminals. A compromised device can expose your personal information, financial details, and even your identity to potential misuse. Think of it like a fortress; strong defenses are essential to keep intruders out. By implementing strong security measures, you fortify your digital world, ensuring your information remains private and your devices function as intended.
Securing a Computer
Robust computer security begins with strong passwords and multi-factor authentication. Regularly updating software and using antivirus software are vital steps. Regular backups of important files are also essential to mitigate the impact of data loss.
Securing a Mobile Phone
Mobile phones are often the target of cyberattacks due to their ubiquitous nature. Strong passwords, enabling multi-factor authentication, and regularly updating operating systems are critical. Activating features like device encryption and location restrictions can add an extra layer of security.
Securing a Tablet
Tablets, while often seen as less vulnerable, are still susceptible to security threats. Protecting tablets requires the same vigilance as computers and mobile phones. Use strong passwords, enable multi-factor authentication, and keep the software updated.
Setting Up Strong Passwords and Multi-Factor Authentication
Creating strong passwords is a fundamental step in device security. Avoid easily guessable passwords like “password123” or your birthday. Use a combination of uppercase and lowercase letters, numbers, and symbols. Multi-factor authentication adds an extra layer of security by requiring multiple verification methods, such as a code sent to your phone. This makes it significantly harder for attackers to access your accounts, even if they manage to guess your password.
Securing Wireless Networks
Securing your wireless network is crucial. Change the default network name and password. Enable WPA2 or WPA3 encryption to protect data transmitted over the network. Avoid using open Wi-Fi networks for sensitive activities, as they often lack security measures.
Regular Software Updates
Regular software updates are essential for patching security vulnerabilities. Cybercriminals constantly develop new ways to exploit weaknesses in software. By staying updated, you’re installing the latest security patches, minimizing your exposure to known threats.
Creating a Secure Wi-Fi Network
To create a secure Wi-Fi network, follow these steps:
- Change the default network name (SSID) and password.
- Enable WPA2 or WPA3 encryption for enhanced security.
- Use a strong password, incorporating a mix of uppercase and lowercase letters, numbers, and symbols.
- Consider using a password manager for safe storage of your network credentials.
- Avoid using open Wi-Fi networks for sensitive activities.
Security Measures for Different Devices
| Device | Password Strength | Multi-Factor Authentication | Software Updates | Wireless Security |
|---|---|---|---|---|
| Computer | Strong, unique passwords | Enable wherever possible | Regular updates for OS and applications | WPA2/WPA3 encryption, strong network password |
| Mobile Phone | Strong, unique passwords | Enable wherever possible | Regular OS updates | WPA2/WPA3 encryption, strong network password |
| Tablet | Strong, unique passwords | Enable wherever possible | Regular OS updates | WPA2/WPA3 encryption, strong network password |
Data Protection and Privacy
Your digital life is a treasure trove of personal information. From online banking details to social media posts, everything you do online leaves a digital footprint. Understanding how to protect this data is crucial for maintaining your privacy and security. Data protection isn’t just about avoiding hackers; it’s about safeguarding your identity and well-being in the digital age.
Protecting your personal data online requires a multi-faceted approach. It’s not just about installing software; it’s about understanding the risks and adopting responsible digital habits. Think of it like safeguarding a physical treasure – you need a combination of locks, alarms, and vigilance to keep it safe.
Protecting Personal Information Online
Safeguarding your personal information online involves a series of proactive steps. This is about more than just password strength; it’s about building a comprehensive defense against digital threats. The key is to be aware of the potential risks and take steps to mitigate them.
- Strong Passwords and Authentication: Use unique and complex passwords for each online account. Avoid easily guessable passwords like your pet’s name or birthdate. Enable two-factor authentication whenever possible. This adds an extra layer of security, requiring a code sent to your phone or email in addition to your password.
- Regularly Updating Software and Devices: Software updates often include security patches to fix vulnerabilities. Outdated software can be a prime target for hackers. Regularly update your operating system, applications, and security software to stay ahead of potential threats.
- Be Wary of Public Wi-Fi: Public Wi-Fi networks are often unsecured. Avoid accessing sensitive information like banking details or personal documents on these networks. If you absolutely need to, use a Virtual Private Network (VPN) to encrypt your connection.
Identifying and Avoiding Phishing Attempts
Phishing scams are designed to trick you into revealing personal information. They often mimic legitimate websites or emails. Be extremely cautious of any communication asking for your login credentials, banking information, or personal details.
- Verify the Sender’s Identity: Don’t click on links in emails or messages from unknown senders. If you’re unsure, contact the company or organization directly using a known phone number or website address.
- Check for Red Flags: Look for grammatical errors, suspicious URLs, or generic greetings in emails or messages. These are often telltale signs of a phishing attempt. Pay attention to the sender’s email address – is it a legitimate domain? Does it match the sender’s name or the organization they claim to represent?
- Hover Over Links Carefully: Before clicking on a link, hover your mouse over it to see the actual URL. If the URL looks suspicious or different from what you expect, don’t click it.
Protecting Sensitive Data
Sensitive data, such as financial information and personal documents, requires extra protection. Think of it like a vault – you need strong locks and multiple layers of security.
- Use Strong Encryption: Encrypt sensitive files and data using encryption software. This will make your information unreadable to unauthorized individuals.
- Employ Secure Storage Methods: Store sensitive data in secure locations, such as encrypted cloud storage or password-protected folders on your computer. Limit access to these files to only authorized personnel.
- Regularly Review and Update Privacy Settings: Review and update your privacy settings on all your online accounts to control what information is shared.
Significance of Privacy Settings and Controls
Privacy settings and controls allow you to customize how your data is collected, used, and shared online. Understanding these settings is crucial for maintaining control over your personal information.
- Understand Your Account Settings: Take the time to understand the privacy settings on your social media accounts, email platforms, and online banking portals. Customize these settings to limit data collection and sharing.
- Enable Two-Factor Authentication: Enabling two-factor authentication adds an extra layer of security to your accounts. This is a critical measure to protect against unauthorized access.
- Be Aware of Data Collection Practices: Be aware of the data collection practices of the websites and applications you use. Know what information they are collecting and how they are using it.
Importance of Secure Browsing Habits
Secure browsing habits are essential for protecting yourself from online threats. It’s about making smart choices when using the internet.
- Use HTTPS: Prioritize websites that use HTTPS (Hypertext Transfer Protocol Secure). This protocol encrypts your communication with the website, ensuring your data is protected.
- Be Cautious of Downloads: Only download software and files from trusted sources. Be wary of downloading files from unknown or suspicious websites.
- Avoid Clicking on Suspicious Links: Don’t click on links or attachments from unknown or untrusted sources. If you’re unsure, contact the sender directly through a known method.
Recognizing and Reporting Suspicious Emails or Messages
Identifying and reporting suspicious emails or messages is crucial for protecting yourself and others. It’s about being vigilant and acting on potential threats.
- Look for Red Flags: Be on the lookout for unusual requests, grammatical errors, and suspicious links in emails or messages. If something seems off, treat it with extreme caution.
- Report Suspicious Emails or Messages: Report suspicious emails or messages to the relevant authorities or organizations. This helps prevent further harm and protect others from similar scams.
Building a Secure Digital Lifestyle
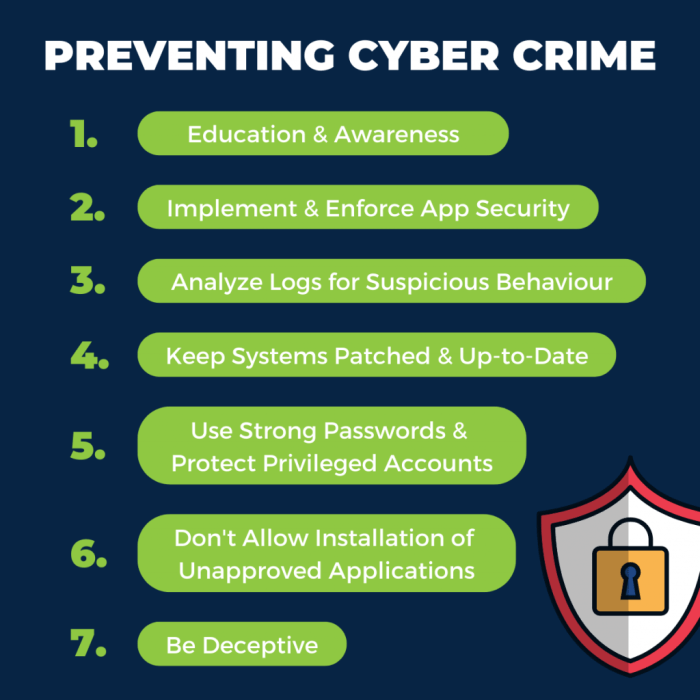
Source: shortpixel.ai
Navigating the digital world safely requires more than just knowing about viruses and firewalls. It’s about adopting a holistic approach to online security, integrating safety measures into your daily digital routine. This involves understanding the potential risks, taking proactive steps, and fostering a mindful online presence. It’s about building a secure digital lifestyle that protects your personal information and keeps you safe from harm.
A secure digital lifestyle isn’t just about avoiding trouble; it’s about proactively managing your online footprint. It’s about making informed decisions, understanding the risks, and creating habits that empower you to stay safe and secure in the digital realm. This means taking control of your online identity and taking responsibility for your digital security.
Safe Online Behaviors
Maintaining a secure online presence involves conscious choices in how you interact with the digital world. Being aware of potential dangers and implementing safety measures is crucial for protecting yourself from various online threats. Avoid sharing sensitive personal information unnecessarily, especially on public forums or unverified websites. Be wary of suspicious links or emails, and always verify the source before clicking or opening.
Strong Passwords and Password Managers
Strong passwords are your first line of defense against unauthorized access. Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names. Consider using a password manager to securely store and manage multiple passwords, streamlining your security practices. Password managers generate and store strong, unique passwords for each of your accounts, reducing the risk of compromised accounts.
Software and Operating System Updates
Regular software and operating system updates are vital for maintaining a secure digital environment. These updates often include critical security patches that address vulnerabilities. Keeping your software current helps to protect your devices from malware and other threats. Patches often fix bugs and address security issues that malicious actors may be exploiting.
Identifying and Avoiding Scams and Online Threats, Cybersecurity for Everyone: Software and Devices to Stay Safe
Scams and online threats are constantly evolving. Be vigilant and skeptical of unsolicited requests for personal information or financial details. Do thorough research on unfamiliar websites or emails before interacting with them. Be aware of phishing scams, which attempt to trick you into revealing your personal information. Always verify the legitimacy of requests for sensitive data.
Reporting Cybercrime and Staying Informed
Reporting cybercrimes to the appropriate authorities is essential for preventing further incidents and holding perpetrators accountable. Understanding how to report cybercrime and staying informed about current threats are crucial parts of maintaining a secure digital lifestyle. Keep abreast of the latest security advisories and best practices to proactively protect yourself.
Online Safety Tips
- General Safety: Avoid sharing personal information unnecessarily online. Verify the legitimacy of websites and emails before clicking or interacting.
- Password Security: Use strong, unique passwords for each account. Employ a password manager to securely store and manage your passwords.
- Software Updates: Regularly update your software and operating systems to benefit from security patches.
- Threat Awareness: Be vigilant about phishing attempts and other scams. Research unfamiliar websites and emails thoroughly before interacting with them.
- Reporting Cybercrime: Report suspected cybercrimes to the appropriate authorities.
Specific Security Considerations for Different Users
Navigating the digital world can feel like a minefield, especially when you’re not entirely sure who’s watching or what’s lurking around every corner. Knowing the specific security challenges faced by different user groups—from kids to seniors to small business owners—is key to staying safe online. Let’s dive into the unique vulnerabilities each group faces and how to protect them.
Understanding the nuances of cybersecurity for different demographics is crucial. Each age group and profession brings unique risks and needs, demanding tailored solutions.
Security Challenges for Children Online
Children are particularly vulnerable online due to their limited understanding of online risks and their often-unsupervised online activity. They are often targets of cyberbullying, online predators, and inappropriate content. This necessitates proactive measures to protect their online safety.
- Cyberbullying and Harassment: Children can be targeted by bullies and harassed online through social media, instant messaging, and gaming platforms. This can lead to significant emotional distress, anxiety, and even depression. Parents and educators need to educate children on recognizing and reporting cyberbullying.
- Online Predators: Children are at risk of encountering online predators who may attempt to groom them for sexual abuse. These predators often use social media and gaming platforms to build relationships with children. Monitoring children’s online activity and teaching them to be cautious about sharing personal information is crucial.
- Inappropriate Content: Children can accidentally or intentionally encounter inappropriate content online, including harmful or disturbing images and videos. Filtering and monitoring their online activities, and having open conversations about internet safety are key.
Protecting Children’s Online Accounts
Protecting children’s online accounts involves a multi-faceted approach, encompassing parental controls, strong passwords, and open communication.
- Parental Controls: Implementing parental controls on devices and online accounts allows parents to filter inappropriate content, monitor online activity, and limit access to certain websites. This provides a layer of protection against harmful content and interactions.
- Strong Passwords: Teaching children to create and use strong, unique passwords for each account is crucial. Explain the importance of not sharing passwords with anyone.
- Open Communication: Establish open communication channels with children about online safety. Explain the risks they might face and encourage them to report any suspicious activity or uncomfortable situations.
Security Issues for Seniors
Seniors often face unique challenges online, including difficulties with technology, limited knowledge of cybersecurity, and increased vulnerability to scams and fraud. Strategies to address these challenges are vital for their safety and well-being.
- Technical Challenges: Seniors may experience difficulties with navigating online platforms, understanding security protocols, and using complex software. This can make them more susceptible to scams and malware.
- Limited Cybersecurity Knowledge: Seniors may lack the knowledge or experience to identify phishing scams, malware, or other online threats. Education and support are crucial in this context.
- Financial Scams: Seniors are often targeted by financial scams, including investment fraud, romance scams, and lottery scams. They may be more trusting and less aware of the risks involved.
Security Considerations for Small Business Owners
Small business owners often juggle many responsibilities, and cybersecurity can sometimes be overlooked. Their businesses are vulnerable to various cyberattacks, including ransomware, phishing, and malware.
- Ransomware Attacks: Small businesses are increasingly targeted by ransomware attacks, which can cripple operations and lead to significant financial losses. Implementing robust backups and security measures is critical.
- Phishing Scams: Phishing emails and websites can compromise sensitive data, leading to financial losses and reputational damage. Training employees to identify and avoid phishing attempts is vital.
- Malware Infections: Malware can infiltrate systems, steal data, and disrupt operations. Implementing robust antivirus software and regular security updates is essential.
Comparison Table of Security Concerns and Solutions
| User Group | Security Concerns | Solutions |
|---|---|---|
| Children | Cyberbullying, predators, inappropriate content | Parental controls, strong passwords, open communication |
| Seniors | Technical difficulties, limited knowledge, financial scams | Simplified interfaces, educational resources, fraud awareness |
| Small Businesses | Ransomware, phishing, malware | Robust backups, employee training, security updates |
Illustrative Examples of Secure Practices
Staying safe online isn’t just about knowing the rules; it’s about applying them in real-world scenarios. This section dives into practical examples, showing how everyday actions can significantly bolster your digital defenses. From choosing strong passwords to spotting sneaky phishing attempts, these illustrations will empower you to navigate the digital landscape with confidence and security.
Secure Software Usage
Software is the backbone of our digital lives, but not all software is created equal. Understanding how to use it securely is crucial. Installing updates promptly is vital for patching vulnerabilities. This proactive measure minimizes the risk of exploits, ensuring your software remains robust against evolving threats. Using trusted software sources is equally important. Downloading from official websites or reputable app stores drastically reduces the chance of encountering malware disguised as legitimate applications. Consider employing a reputable antivirus program, a critical tool that detects and removes malicious software.
Identifying and Avoiding Phishing Attacks
Phishing attacks are sophisticated attempts to trick you into revealing sensitive information. Recognizing these tactics is paramount for avoiding becoming a victim. Look for suspicious emails with poor grammar, urgent requests, or unfamiliar sender addresses. Hover over links before clicking to check the actual destination URL; a subtle difference can be the key to identifying a fraudulent link. Be wary of emails promising prizes or demanding immediate action. Verify information directly with the source rather than relying on suspicious communications.
Strong Passwords and Password Management
Strong passwords are the first line of defense against unauthorized access. A strong password combines uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or pet names. Employing a password manager is another crucial step. These tools securely store and generate complex passwords, eliminating the need to memorize them all. Consider using a unique password for each online account to prevent a breach from compromising multiple accounts.
Secure Browsing Practices
Browsing securely involves several key practices. Use HTTPS whenever possible. This protocol ensures encrypted communication between your browser and the website, protecting your data from eavesdropping. Be cautious about clicking on unknown links or downloading files from untrusted sources. This single act can lead to malware infection or data breaches. Regularly clear your browser’s cache and cookies to protect your privacy and reduce the risk of tracking. Employ a VPN for added security when using public Wi-Fi networks.
Secure Device Configurations
Different devices require different security configurations. Mobile devices benefit from enabling two-factor authentication (2FA) for added protection. Regularly checking and updating the device’s operating system is crucial to ensure security patches are applied. Enable device encryption to safeguard your data even if the device is lost or stolen. Set up strong passcodes for all your devices, and consider using biometric authentication for extra security.
Configuring Secure Wi-Fi
Securing your Wi-Fi network is crucial for preventing unauthorized access. Change the default network name (SSID) and password. Use a strong, complex password that’s difficult to guess. Enable WPA2 or WPA3 encryption to protect your network. Limit access to your network to only authorized devices. Consider using a firewall to filter incoming and outgoing network traffic. This table summarizes the steps:
| Step | Action | Visual Description |
|---|---|---|
| 1 | Change SSID and Password | (Imagine a network settings page with input fields for SSID and password.) |
| 2 | Enable WPA3 Encryption | (Imagine a network settings page with a toggle switch for WPA3 encryption.) |
| 3 | Limit Access to Devices | (Imagine a network settings page with a list of connected devices, with options to restrict access.) |
| 4 | Use a Firewall | (Imagine a network settings page with a firewall configuration option.) |
Using strong passwords, enabling encryption, and regularly updating your software are all essential steps for a more secure digital life.
Last Point

Source: twimg.com
In conclusion, Cybersecurity for Everyone: Software and Devices to Stay Safe emphasizes that safeguarding yourself online requires a multifaceted approach. By understanding the common threats, utilizing the right software, and adopting secure practices, you can build a strong defense against cyber risks. Remember, proactive measures are key to maintaining your digital well-being. Stay informed, stay secure.